Welcome back, my amateur hackers!
With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.
Any time someone's computer seems to act on its own volition, it tends to freak people out. When it acts on its own volition and opens up the user's own obituary (death notice), we are sure to get a decent reaction.
In this hack, we will create an obituary for our victim, then open their web browser right to it so that it appears as if the computer is haunted. It is certain to make them feel like something unearthly is happening.
Step 1: Fire Up Kali
The first step, of course, is to fire up Kali. I'm using Kali 1.1, but you can use any version of Kali for this hack.
Step 2: Exploit the Victim's Computer
Before we do anything, we need to own the victim's computer.
There are many ways to exploit their computer. Since we are likely on the same network as the victim (how else will we be able to enjoy their reaction if we are not nearby?), it makes it even easier. If we have physical access to system, even for a few seconds, we could install a Metasploit payload or Netcat in a few seconds.
Below is a list of just a few ways (with instructions) to exploit your victim's system for this ghoulishly good Halloween prank.
- Using a malicious PDF
- Using a malicious Word .doc
- Using Flash-based exploits
- Hooking the browser with BeEF
- Using a man-in-the-middle attack
- Using a malicious link file
- Using a malicious Windows Media Center link (.mcl)
And there are many more. Take a look through my many tutorials here on Null Byte and you will find almost innumerable ways to compromise somebody's computer.
Step 3: Build an Obituary
Now that we have compromised the victim's computer, let's build their obituary. There are numerous free website/blog builders out there such as Blogger, Weebly, Wix, WordPress, etc. In this case, I built an obituary using the free website builder, WordPress.
I hope it goes without saying, build your own obituary for your own victim. Mine is simple and only meant as a example. You might want to put in some personal details about your victim that would make it seem more realistic, maybe even humorous.
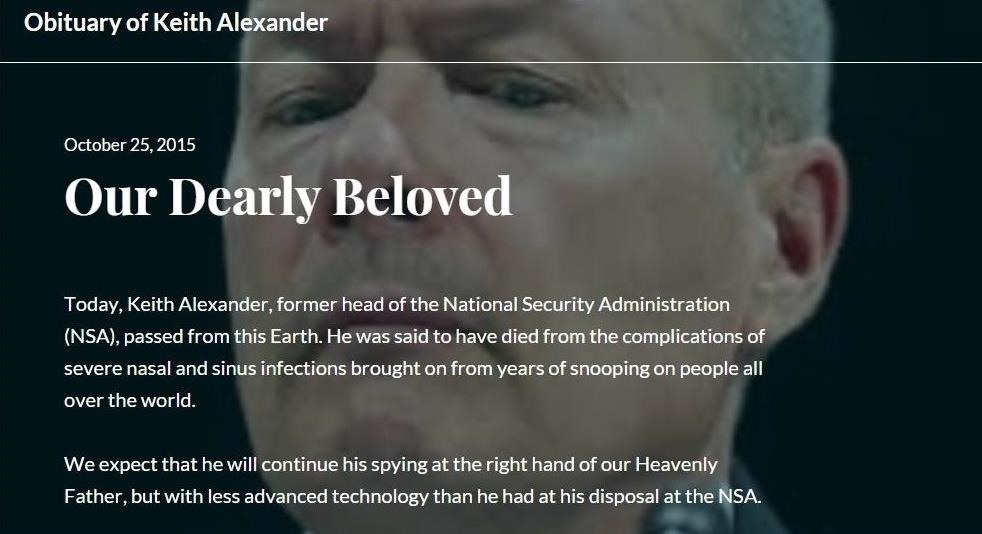
Step 4: Direct Their Browser to the URL
Now that we have the victim's obituary built, the next step is to open their web browser to their own obituary page.
Since we have a command prompt on the remote system, we can simply start Internet Explorer to open the URL of the obituary (you can use Firefox just as easily). For more info on using the CMD prompt on a remote system, see my article here.
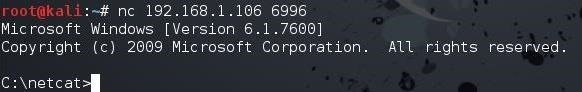
To open their Internet Explorer, I need to navigate to the directory of IE.
c:\cd c:\Program Files(x86)\Internet Explorer
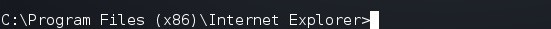
Now, to open their IE browser to his/her obituary, I can simply type:
c:\Program Files (x86)\Intenet Explorer\iexplore https:/bossobit.wordpress.com
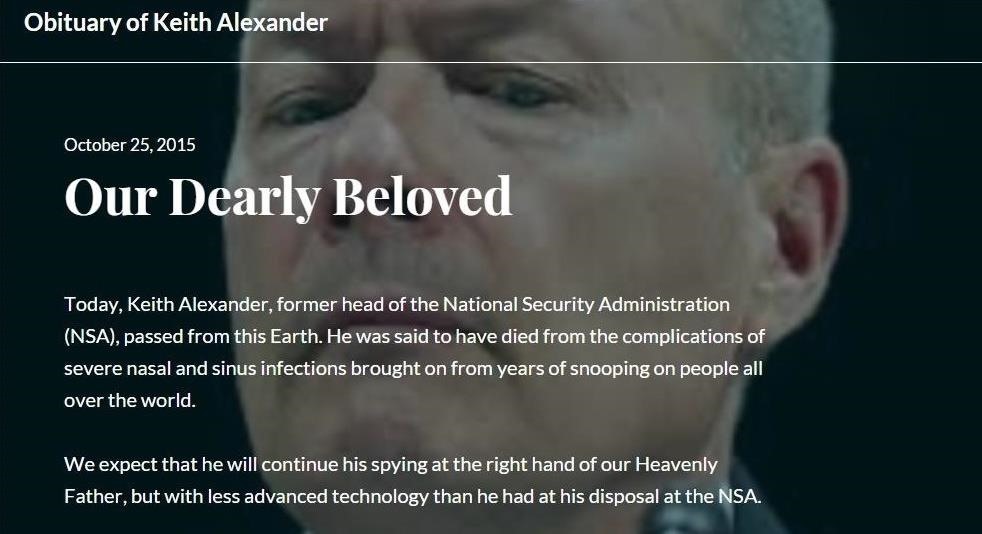
If the browser opening on its own as if haunted doesn't freak them out, seeing their own obituary online certainly will.
Keep coming back, my amateur hackers, to continue to learn the techniques and tools of the future's most valuable skill set—hacking!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























20 Comments
NIce one...although id probably get fired doing this :)
Nice job OTW.
Good one. My boss unfortunately is an avid Mac user and that's a world I haven't ventured into yet. Maybe next Halloween.
That's OK. Just use a Mac exploit.
You are teaching the things I've been looking for for the last 3 years and never knew where to start. Just by reading and following your examples gets me to a good level Wht hckr. Thank you OTW
I'm glad you found us.
I'm glad too...you know good things come to those who wait :)
Wouldnt your boss fire you for violating his privacy?
That depends on your boss. Mine wouldn't.
i we have physical access ... how can a metasploit payload be installed
Use msfvenom to embed a payload in an exe then put it on a flash drive, take it to his machine and execute it. Make sure you have the multi handler open on your attacking machine.
Can we also send the exe through email if the human is gulable enough?
OTW is correct, although you can write a PHP script which redirects to a exe. In the email itself, the url will just look like an ordinary get request to a site. I guess you could also do this using a Javascript redirect.
Another thing you may find is, that IE/Chrome are actually very good at reading signatures now adays, you could probably just about get away with a media center exploit.
HOW NICE_
Most web based email will not allow you to send an exe.
I had not test but when i was read the project i thought it might be true
You mention, "Since we are likely on the same network as the victim (how else will we be able to enjoy their reaction if we are not nearby?), it makes it even easier." Can you explain how that is? Is there a technique where ones we're in the same network, its a simple command to take over the machine? Or its still the same way were they must still click on something?
Are you still employed
Just found this article and wow haha I cant wait to try this
use ettercap for DNS spoofing and PHP for hosting
much easier
Share Your Thoughts